Practical Reverse Engineering Sample D
Overview
I will be reverse engineering Sample D from Practical Reverse Engineering
This includes answering questions about the sample from the book as well as looking into other parts of the sample (if found to be interesting)
You can grab the samples from here
Taking a glance
The first thing I want to check if the sample if intended for x86 or x64 using PEbear.
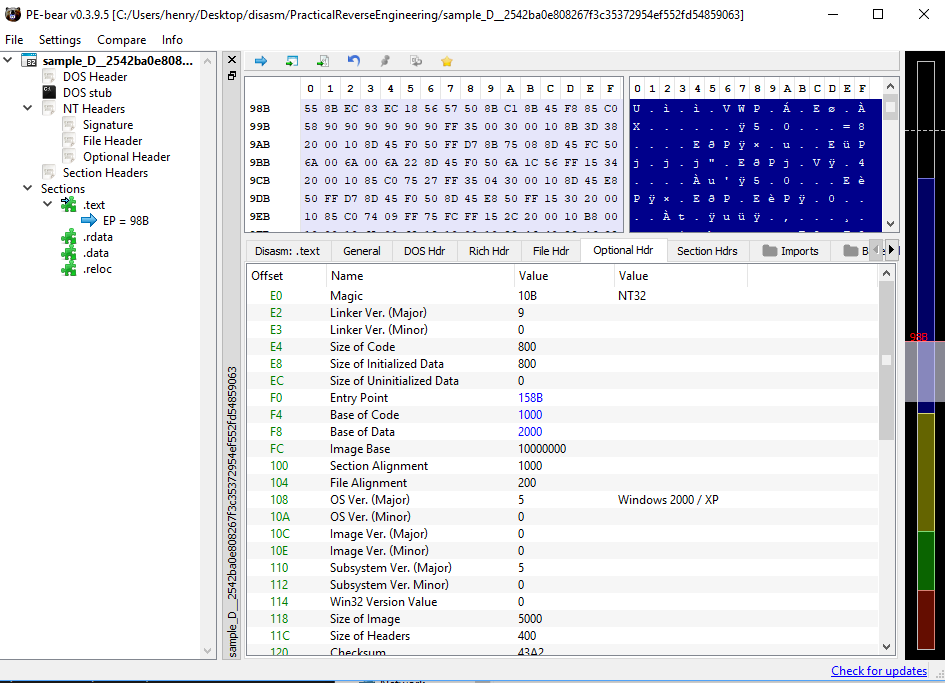
As shown, it is an x86 sample
Loading into IDA, there only 6 functions written by the author (excluding import calls), which is really nice (beginner kernel malware to start reverse engineering with)
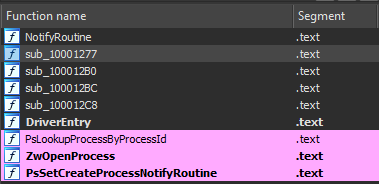
Tackling the questions!
In the book on page 184, question 1 is as stated:
(Sample D)
Analyze and explain what the function 0x10001277 does.
Where does the second argument come from and can it ever be invalid?
What do the functions at offset 0x100012B0 and 0x100012BC do?
0x10001277
Whole function in IDA:
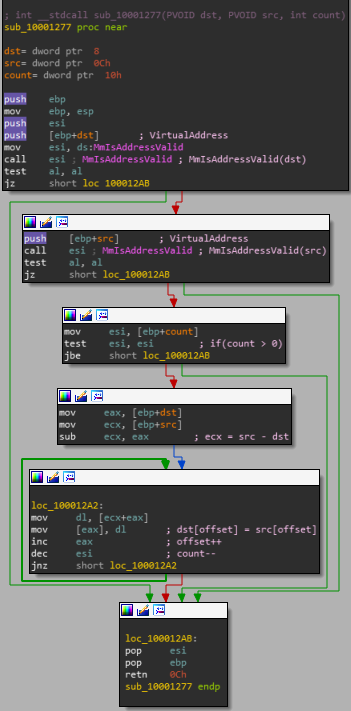
Let’s start at the top:
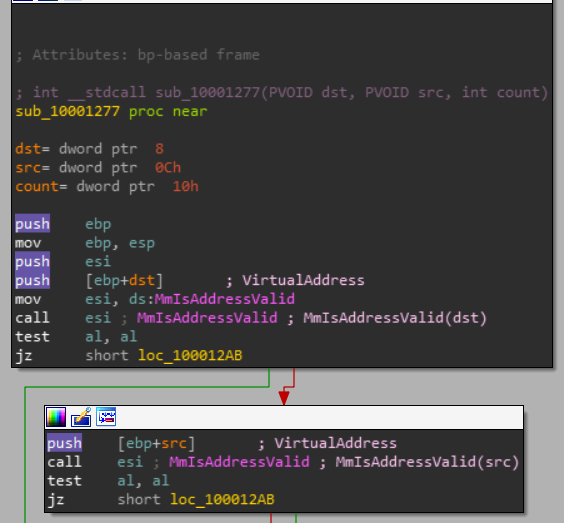
This part can be broken down into just two checks for dst and src.
if(MmIsAddressValid(dst) && MmIsAddressValid(src)) {
...
}
Afterwards,
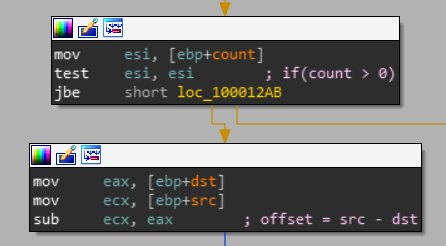
The third argument is count, which has to be positive and src is subtracted from dst to get the offset.
if(count > 0) {
size_t offset = src - dst;
...
}
Lastly,
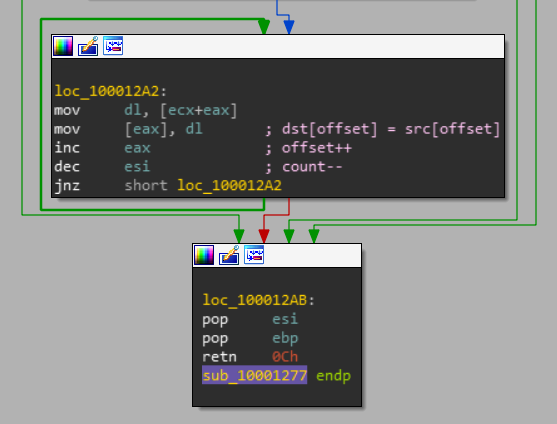
Use of [ecx + eax] is essentially an array index to a pointer and afterwards, it the value is copied to the src pointer at an index.
Basically, an inline memcpy is implemented here.
This is done until esi is zero.
memcpy(src, dst, count);
Decompiled:
void sub_10001277(PVOID dst, PVOID src, size_t count)
{
if(MmIsAddressValid(dst) && MmIsAddressValid(src) && count) {
memcpy(src, dst, count);
}
}
Where does the second argument come from and can it ever be invalid?
Take a look at the xrefs:
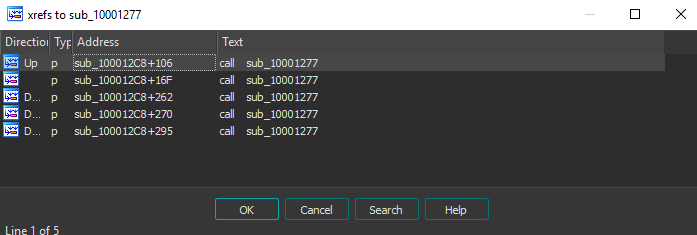
The first two xrefs:
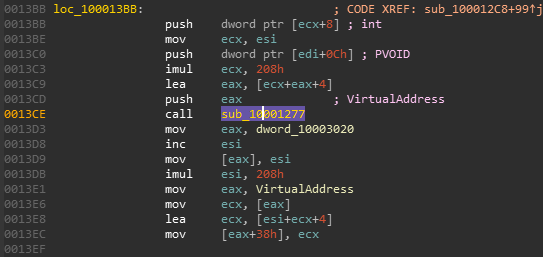
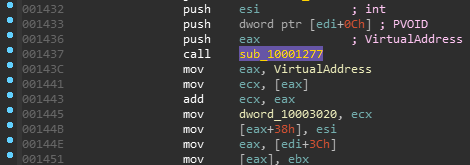
These both reference [edi + 0Ch]. In the beginning of the function, IDA labels edi as Irp.
What is at the offset at 0Ch of Irp?
Enjoy Reading This Article?
Here are some more articles you might like to read next: